As we navigate the complexities of data protection, understanding encryption is crucial. It serves as a vital safeguard against unauthorized access, ensuring that sensitive information remains confidential. For those interested in enhancing their digital projects, exploring resources like bag mockups can provide valuable insights.
In an era where data breaches and cyber threats are ever-present, understanding how encryption works is paramount. Encryption serves as a robust mechanism to safeguard sensitive information, ensuring that only authorized individuals can access it. Whether it’s personal data, corporate secrets, or financial transactions, encryption plays a critical role in maintaining confidentiality and integrity. In this article, we will explore the foundational aspects of encryption, its various types, and its applications in today’s digital landscape.
What is Encryption?
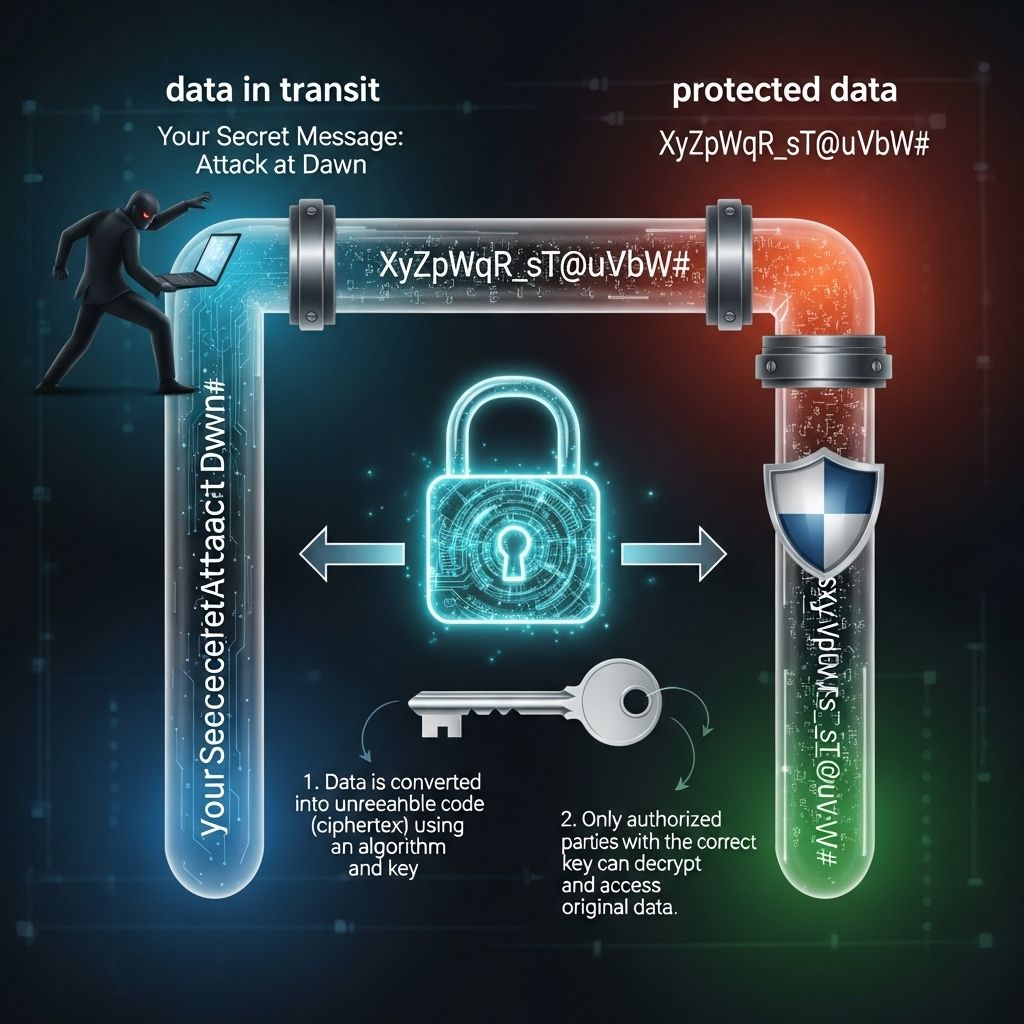
Encryption is a process that transforms readable data, known as plaintext, into an unreadable format called ciphertext. This transformation is executed using algorithms and keys, which are essential components in the encryption process. The primary goal is to protect data from unauthorized access and ensure that even if data is intercepted, it remains secure and unintelligible.
The Basics of Encryption
The encryption process involves two main components:
- Encryption Algorithm: A mathematical process used to perform the encryption and decryption of data.
- Encryption Key: A string of characters used by the algorithm to convert plaintext into ciphertext and vice versa.
Types of Encryption
Encryption can be categorized into two main types: symmetric encryption and asymmetric encryption. Each has its unique features and use cases.
Symmetric Encryption
Symmetric encryption uses a single key for both encryption and decryption. This means that the same key must be kept secret and shared between the sender and recipient. Examples include:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- RC4
Pros and Cons of Symmetric Encryption
| Pros | Cons |
|---|---|
| Fast and efficient for large data sets | Key distribution can be a challenge |
| Less computational overhead | If the key is compromised, the data is at risk |
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, utilizes a pair of keys: a public key for encryption and a private key for decryption. This method eliminates the need for key sharing. Popular examples include:
- RSA (Rivest-Shamir-Adleman)
- Elliptic Curve Cryptography (ECC)
Pros and Cons of Asymmetric Encryption
| Pros | Cons |
|---|---|
| Secure key exchange | Slower than symmetric encryption |
| Reduces the risk of key compromise | More computationally intensive |
How Encryption Works
To understand how encryption works, let’s break down the process into a few key steps:
- Plaintext Generation: The original data that needs to be protected.
- Key Creation: A secure key is generated using algorithms.
- Encryption Process: The encryption algorithm transforms the plaintext into ciphertext using the key.
- Transmission/Storage: The ciphertext is securely transmitted or stored.
- Decryption Process: The authorized party uses the appropriate key and algorithm to convert the ciphertext back into plaintext.
Applications of Encryption
Encryption has a myriad of applications across various domains, including:
1. Data at Rest
Data stored on devices, such as computers and servers, can be encrypted to prevent unauthorized access. For instance:
- Full Disk Encryption (FDE) for laptops and mobile devices
- Database encryption to safeguard sensitive records
2. Data in Transit
When data is transmitted over networks, encryption ensures its confidentiality. Common applications include:
- HTTPS (HyperText Transfer Protocol Secure) for secure web browsing
- VPN (Virtual Private Network) connections to secure remote access
3. Email Encryption
Protecting email communications is vital for privacy. Methods include:
- PGP (Pretty Good Privacy)
- S/MIME (Secure/Multipurpose Internet Mail Extensions)
The Future of Encryption
As technology advances, so do the threats to data security. The future of encryption will likely be shaped by:
1. Quantum Computing
The rise of quantum computers poses a challenge to traditional encryption methods. Researchers are exploring quantum-resistant algorithms that can withstand potential attacks from quantum systems.
2. Increased Regulation
With data privacy laws like GDPR and CCPA, there will be an increased emphasis on encryption as a requirement for compliance.
3. Standardization of Protocols
The industry will likely see a push towards standardizing encryption protocols to enhance interoperability and security across platforms.
Conclusion
Encryption is an essential tool for protecting data in our increasingly digital world. Understanding how it works, its types, and its applications can empower individuals and organizations to make informed decisions about data security. As threats evolve, so too must our strategies for safeguarding information, making encryption more critical than ever.
FAQ
What is encryption and how does it work?
Encryption is the process of converting data into a coded format that cannot be easily read by unauthorized users. It uses algorithms and keys to transform plain text into ciphertext.
Why is encryption important for data protection?
Encryption is crucial for protecting sensitive information from cyber threats, ensuring that only authorized users can access and read the data, thereby maintaining confidentiality and integrity.
What types of encryption methods are commonly used?
Common encryption methods include symmetric encryption, where the same key is used for both encryption and decryption, and asymmetric encryption, which uses a pair of keys—one public and one private.
How does encryption help in compliance with data protection regulations?
Encryption helps organizations comply with data protection regulations like GDPR and HIPAA by safeguarding personal and sensitive information, thus reducing the risk of data breaches and penalties.
Can encryption protect data in transit and at rest?
Yes, encryption can protect data both in transit (when being sent over networks) and at rest (when stored on devices or servers), ensuring that it remains secure in both states.