In today’s competitive landscape, enhancing your SaaS offerings requires not only innovative features but also top-notch security measures. Exploring effective strategies for cloud security management is essential to safeguard your operations and data. For those looking to elevate their branding efforts alongside security, consider leveraging mockup templates for bags to visualize your product designs.
In today’s digital landscape, where Software as a Service (SaaS) applications have become the backbone of many businesses, ensuring robust cloud security management is paramount. With the increasing adoption of cloud technologies, organizations must navigate the complex terrain of security challenges that come with storing sensitive data and running critical applications in the cloud. This article delves into essential strategies and best practices to elevate your SaaS with effective cloud security management, ensuring your data remains safe and compliant.
The Importance of Cloud Security Management
Cloud security management refers to the policies, technologies, and controls that protect cloud data, applications, and infrastructure from threats. With the rise of cyber attacks and data breaches, the need for a comprehensive security strategy has never been more pressing. Here are some key reasons why cloud security management is critical:
- Data Protection: Safeguarding sensitive information from unauthorized access and breaches.
- Compliance: Adhering to regulations such as GDPR, HIPAA, and others that mandate strong security protocols.
- Reputation Management: Protecting your brand’s reputation by avoiding data leaks that can harm customer trust.
- Operational Continuity: Ensuring that your SaaS applications remain operational even in the event of a security incident.
Risk Assessment and Management
Before implementing any security measures, it’s crucial to conduct a thorough risk assessment. This process involves identifying potential vulnerabilities in your systems and evaluating their potential impact on your business. Here’s how to approach risk assessment effectively:
Steps for Conducting a Risk Assessment
- Identify Assets: List all your cloud-based assets, including applications, data, and users.
- Identify Threats: Determine potential threats such as cyber attacks, insider threats, and natural disasters.
- Evaluate Vulnerabilities: Assess weaknesses in your infrastructure that could be exploited by threats.
- Analyze Risks: Evaluate the likelihood and impact of each identified risk on your organization.
- Prioritize Risks: Rank risks based on their severity to focus your security efforts where they matter most.
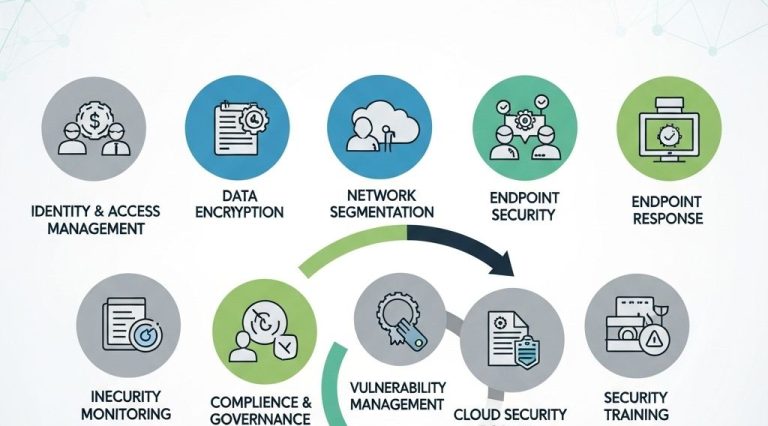
Implementing Security Controls
Once you’ve assessed your risks, the next step is implementing the right security controls. Various frameworks and technologies can help you bolster your cloud security:
Layered Security Approach
A layered security approach, or defense-in-depth strategy, involves employing multiple security measures to protect your SaaS from evolving threats. This includes:
| Layer | Security Measure |
|---|---|
| Perimeter Security | Firewalls, intrusion detection systems (IDS) |
| Network Security | Virtual private networks (VPNs), network segmentation |
| Application Security | Application firewalls, regular updates and patches |
| Data Security | Encryption, data masking, tokenization |
| User Security | Multi-factor authentication (MFA), role-based access control (RBAC) |
Utilizing Cloud Security Tools
Investing in cloud security tools can enhance your organization’s ability to monitor and protect your applications:
- Cloud Access Security Brokers (CASBs): Act as intermediaries between users and cloud service providers to enforce security policies.
- Security Information and Event Management (SIEM): Provides real-time analysis of security alerts generated by applications and network hardware.
- Identity and Access Management (IAM): Ensures that the right individuals have the appropriate access to cloud resources.
- Vulnerability Management Tools: Automate the process of scanning and patching vulnerabilities in your software.
Data Encryption and Backup
Data encryption is a vital component of cloud security management. Encrypting data at rest and in transit minimizes the risk of exposure during a breach. Here are best practices for encryption:
Best Practices for Data Encryption
- Use Strong Encryption Standards: AES-256 is widely regarded as a secure encryption standard.
- Encrypt Sensitive Data Only: Focus your encryption efforts on sensitive information to optimize performance.
- Regularly Update Encryption Keys: Rotate keys periodically to enhance security.
Alongside encryption, regular data backups are essential for operational continuity. Implement an automated backup strategy that includes:
- Frequent backups (daily or weekly)
- Offsite storage for disaster recovery
- Regular testing of backup restoration processes
Employee Training and Awareness
Human error remains one of the leading causes of security breaches. Regular training and awareness programs for employees can significantly reduce the risk of accidental data exposure. Here’s how to implement an effective training program:
Creating a Security Awareness Program
- Define Key Security Topics: Focus on phishing, password management, and data handling practices.
- Offer Regular Training Sessions: Conduct workshops, webinars, or e-learning to keep security top of mind.
- Simulate Phishing Attacks: Test employees’ responses to phishing attempts to reinforce learning.
Continuous Monitoring and Improvement
Cloud security management is not a one-time effort; it requires ongoing monitoring and improvement. Implement the following:
Regular Security Audits
Conduct regular audits to evaluate the effectiveness of your security controls and policies. This can involve:
- Internal assessments to identify compliance gaps
- External audits by third-party security firms
- Regular updates to security policies based on audit findings
Incident Response Plan
Prepare an incident response plan to address security incidents swiftly:
- Define Roles and Responsibilities: Clearly outline who is responsible for different aspects of incident response.
- Establish Communication Protocols: Ensure that all stakeholders know how to report incidents.
- Conduct Regular Drills: Test the incident response plan to identify areas for improvement.
Conclusion
In the ever-evolving landscape of cloud technology, elevating your SaaS with effective cloud security management is crucial for protecting sensitive data and maintaining customer trust. By implementing a comprehensive security strategy that encompasses risk assessment, layered security controls, data encryption, employee training, and continuous monitoring, organizations can mitigate risks and ensure operational continuity. Embrace the challenge of cloud security management as an integrated part of your business strategy, and you’ll not only protect your assets but also empower your organization to thrive in a competitive market.
FAQ
What is cloud security management for SaaS?
Cloud security management for SaaS refers to the strategies and technologies used to protect software applications hosted in the cloud from unauthorized access, data breaches, and other cybersecurity threats.
Why is cloud security management important for SaaS providers?
Cloud security management is crucial for SaaS providers as it ensures the integrity, confidentiality, and availability of data, helping to build trust with customers and comply with regulatory requirements.
What are the key components of cloud security management?
Key components of cloud security management include identity and access management, data encryption, threat detection, incident response, and compliance monitoring.
How can I improve the security of my SaaS application?
To improve the security of your SaaS application, implement strong authentication mechanisms, regularly update software, conduct security audits, and utilize advanced threat detection tools.
What are common threats to SaaS security?
Common threats to SaaS security include data breaches, account hijacking, phishing attacks, and insecure APIs, all of which can compromise user data and application functionality.
How does cloud security management enhance customer trust?
Effective cloud security management enhances customer trust by demonstrating a commitment to protecting sensitive data, ensuring compliance with regulations, and minimizing the risk of security incidents.