As businesses advance towards cloud integration, understanding security remains pivotal for safeguarding sensitive information. Adopting effective strategies now will not only prepare organizations for the challenges of 2025 but also align with emerging practices in diverse fields, such as exploring unique bag concepts to meet evolving consumer demand.
As organizations increasingly migrate their critical operations to the cloud, the conversation around cloud security becomes not only relevant but essential. With cyber threats evolving at an alarming pace, it is critical for businesses to adopt robust strategies that anticipate future challenges in cloud security. By 2025, the landscape will be significantly different, with emerging technologies and shifts in regulatory frameworks influencing the way we protect data and systems. This article will explore some key strategies for cloud security that organizations should focus on to stay ahead of potential threats.
Understanding the Cloud Security Landscape
Before implementing effective security strategies, it is vital to comprehend the current cloud security landscape. This includes the types of cloud services available, the shared responsibility model, and the potential risks associated with cloud computing.
Types of Cloud Services
- Infrastructure as a Service (IaaS): Virtualized computing resources over the internet.
- Platform as a Service (PaaS): Provides a platform allowing customers to develop, run, and manage applications.
- Software as a Service (SaaS): Software distribution model in which applications are hosted by a service provider and made available to customers over the internet.
The Shared Responsibility Model
The shared responsibility model delineates the security obligations of the cloud provider and the customer. While the cloud provider secures the infrastructure, clients must manage the security of their data and applications.
| Responsibility | Provider | Customer |
|---|---|---|
| Physical Security | X | |
| Network Security | X | |
| Data Security | X | |
| Application Security | X | |
| Identity & Access Management | X |
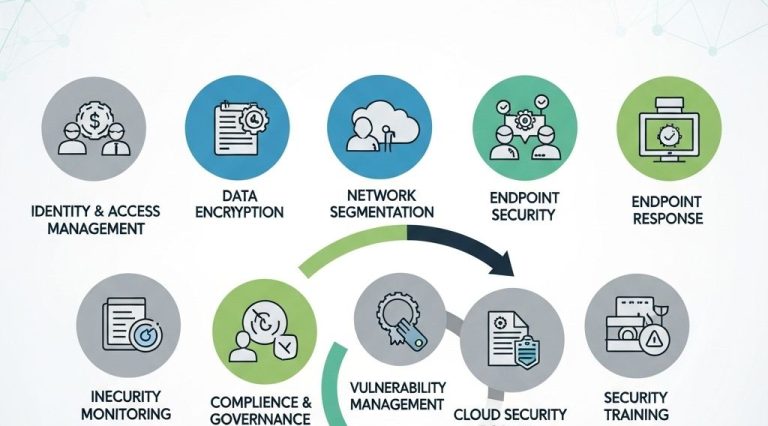
Key Strategies for Enhanced Cloud Security
1. Implement Zero Trust Architecture
Zero Trust is a security concept that revolves around the idea that no one, whether inside or outside the organization, should be trusted by default. By implementing a Zero Trust architecture, organizations can:
- Minimize the attack surface.
- Establish strict identity verification regardless of the user’s location.
- Segment user access to critical assets.
2. Leverage Artificial Intelligence and Machine Learning
AI and machine learning technologies are proving to be game-changers in cloud security. They can be utilized to:
- Detect anomalous behavior across network traffic.
- Automate responses to security incidents.
- Predict potential threats using historical data analysis.
3. Employ Data Encryption Techniques
Data encryption is a critical component of cloud security. Encrypting data both at rest and in transit ensures that sensitive information is protected from unauthorized access. Consider the following:
- Use strong encryption algorithms (e.g., AES-256).
- Manage encryption keys securely using a dedicated key management service.
- Regularly update encryption protocols to counteract evolving threats.
4. Perform Regular Security Audits and Assessments
Continuous monitoring and regular security audits help organizations identify vulnerabilities before they are exploited. Key activities include:
- Penetration testing.
- Compliance checks against industry standards.
- Vulnerability scanning of cloud resources.
Regulatory Compliance and Cloud Security
With the rise of data privacy regulations like GDPR, HIPAA, and CCPA, ensuring compliance has become paramount for organizations. To navigate the regulatory landscape effectively, organizations should:
- Stay updated with regulatory changes affecting cloud operations.
- Implement governance frameworks to ensure compliance.
- Conduct training sessions for employees on compliance requirements.
Future Trends in Cloud Security
As we approach 2025, several trends will shape the future of cloud security:
1. Increased Focus on Privacy-First Technologies
With heightened consumer awareness regarding privacy, companies will need to prioritize technologies that put user privacy first. This includes:
- Implementing privacy-enhancing technologies (PETs).
- Enhancing user consent mechanisms.
- Utilizing data minimization techniques.
2. Growth of Multi-Cloud Strategies
Organizations are increasingly adopting multi-cloud strategies to avoid vendor lock-in and enhance resilience. This approach requires a holistic view on security across multiple cloud environments, ensuring:
- Consistent security policies across platforms.
- Centralized management and monitoring tools.
- Interoperability between different cloud services.
3. DevSecOps Integration
Integrating security into the DevOps pipeline (DevSecOps) ensures that security concerns are addressed from the beginning of the development lifecycle. Benefits include:
- Early detection of vulnerabilities.
- Faster remediation times.
- Enhanced collaboration between development and security teams.
Conclusion
As we look towards 2025, the importance of cloud security cannot be overstated. By adopting a proactive approach that encompasses Zero Trust, AI-driven security, encryption, and regulatory compliance, organizations can not only mitigate risks but also gain a competitive edge in the digital landscape. The rapidly evolving nature of technology necessitates that businesses remain vigilant, adaptable, and forward-thinking in their cloud security strategies to ultimately achieve resilience in an increasingly complex threat environment.
FAQ
What are the top cloud security strategies for 2025?
The top cloud security strategies for 2025 include zero-trust architecture, enhanced encryption protocols, AI-driven threat detection, continuous monitoring, and comprehensive compliance management.
How can organizations implement a zero-trust model in cloud security?
Organizations can implement a zero-trust model by verifying every user and device before granting access to cloud resources, employing micro-segmentation, and using identity and access management (IAM) tools.
What role does AI play in cloud security for 2025?
AI plays a crucial role in cloud security by automating threat detection, analyzing user behavior, and predicting potential vulnerabilities to enhance overall security measures.
Why is encryption important in cloud security?
Encryption is important in cloud security as it protects sensitive data from unauthorized access, ensuring that even if data is intercepted, it remains unreadable without the correct decryption keys.
What are the compliance challenges for cloud security in 2025?
Compliance challenges for cloud security in 2025 include navigating complex regulations, ensuring data sovereignty, and maintaining transparency in data handling practices.
How can continuous monitoring improve cloud security?
Continuous monitoring improves cloud security by providing real-time visibility into security events, allowing organizations to quickly detect and respond to threats before they escalate.