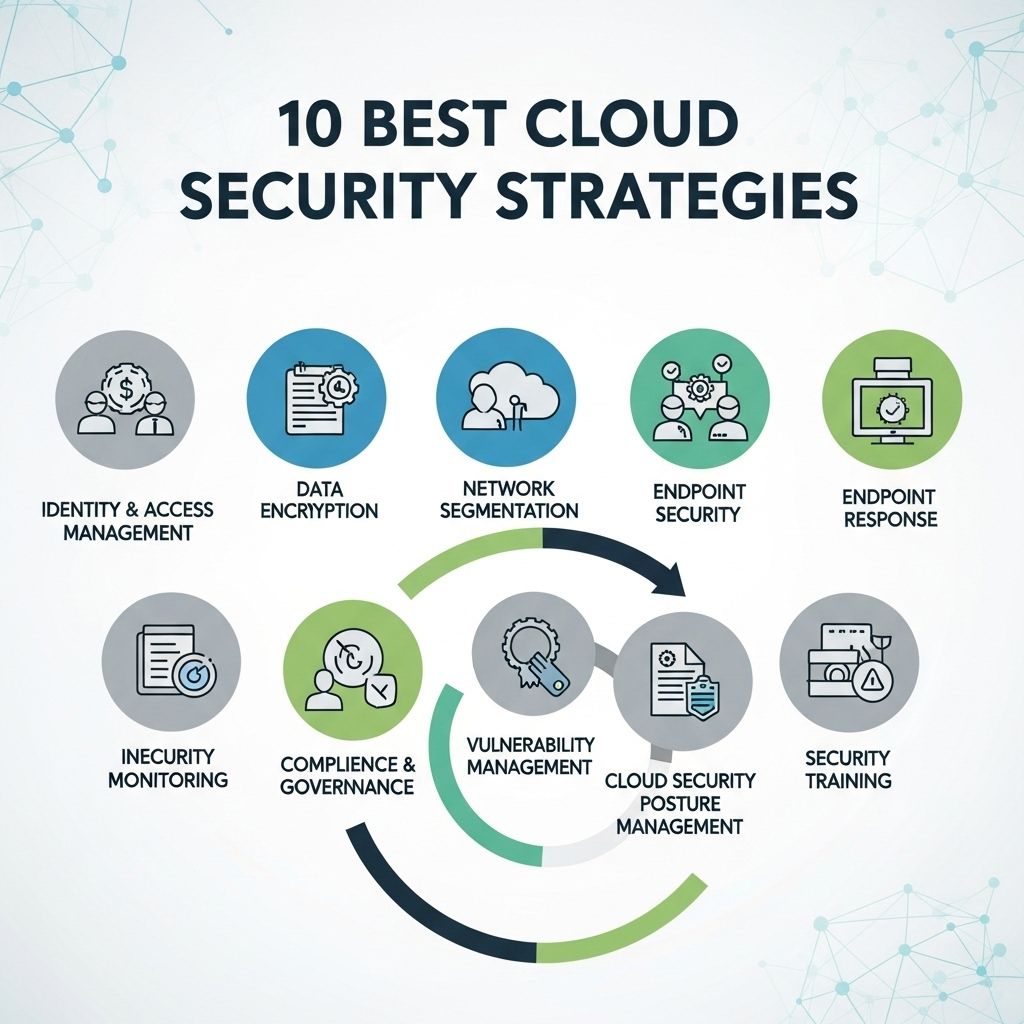
As businesses increasingly migrate to the cloud, ensuring the security of sensitive data has become paramount. Cloud security is not just a matter of compliance; it’s essential for maintaining customer trust and protecting a company’s reputation. In this article, we will explore the top cloud security strategies that organizations can implement to safeguard their data and applications in the cloud.
Understanding Cloud Security
Cloud security encompasses the policies, technologies, and controls that protect cloud computing environments. These strategies are designed to guard against various threats, including data breaches, account hijacking, and insecure APIs. To effectively secure cloud environments, organizations must adopt a multi-layered security approach.
1. Implement Strong Access Controls
Controlling access to cloud resources is the first line of defense in cloud security. Organizations should:
- Utilize role-based access control (RBAC) to ensure that users have the minimum necessary permissions.
- Implement multi-factor authentication (MFA) to add an extra layer of security for user access.
- Regularly review and update access permissions to reflect changes in user roles.
Best Practices for Access Management
Consider the following best practices:
- Use identity and access management (IAM) solutions to enforce policies.
- Monitor user activity for any unauthorized access attempts.
- Educate employees on secure password practices.
2. Encrypt Sensitive Data
Data encryption is crucial for protecting sensitive information. Organizations should:
- Encrypt data both at rest and in transit to mitigate risks of unauthorized access.
- Use strong encryption standards such as AES-256 and RSA.
- Manage encryption keys securely and consider using key management services provided by cloud providers.
Types of Encryption
| Type | Description |
|---|---|
| Symmetric Encryption | Uses the same key for both encryption and decryption. |
| Asymmetric Encryption | Uses a pair of keys (public and private) for encryption and decryption. |
| Hashing | Transforms data into a unique fixed-size string. |
3. Regularly Assess Security Posture
Conducting regular security assessments helps identify vulnerabilities in cloud environments. Organizations should:
- Perform vulnerability scans and penetration testing to uncover security flaws.
- Engage third-party security firms for independent assessments.
- Utilize automated tools for continuous monitoring and alerting.
Assessment Frameworks
Utilize established frameworks, such as:
- NIST Cybersecurity Framework
- ISO/IEC 27001
- Cloud Security Alliance (CSA) Security, Trust & Assurance Registry (STAR)
4. Leverage Security Tools and Technologies
Organizations should take advantage of cloud security tools to enhance their security posture. Some key tools include:
- Cloud Access Security Brokers (CASB)
- Intrusion Detection and Prevention Systems (IDPS)
- Security Information and Event Management (SIEM) systems
Benefits of Automation
Automating security processes can lead to:
- Faster detection of threats
- Reduced response times during incidents
- Minimized human errors in security configurations
5. Train Employees on Security Awareness
Employee training is essential in the fight against cyber threats. Organizations should:
- Conduct regular security awareness training sessions.
- Simulate phishing attacks to educate employees on identifying threats.
- Provide clear reporting channels for suspicious activities.
Topics for Training
Consider covering the following topics in training:
- Identifying phishing and social engineering attacks
- Safe internet browsing practices
- Data handling and privacy policies
6. Ensure Compliance with Regulations
Compliance with industry regulations is vital for cloud security. Organizations should:
- Understand the regulations relevant to their industry (e.g., GDPR, HIPAA, PCI-DSS).
- Implement policies and controls to maintain compliance.
- Document security practices and maintain records for audits.
Compliance Frameworks
Familiarize yourself with compliance frameworks such as:
- NIST
- ISO 27001
- COBIT
7. Utilize Secure APIs
APIs are essential for cloud services but can pose security risks if not properly secured. Organizations should:
- Implement authentication and authorization mechanisms for APIs.
- Regularly test APIs for vulnerabilities.
- Limit the data exposure through APIs to only what is necessary.
API Security Best Practices
Follow these best practices:
- Use HTTPS to encrypt data transmitted through APIs.
- Regularly update and patch API endpoints.
- Monitor API traffic for suspicious activity.
8. Develop an Incident Response Plan
An incident response plan outlines how to respond to security incidents effectively. Organizations should:
- Define roles and responsibilities for the incident response team.
- Establish communication protocols for notifying stakeholders.
- Regularly test and update the incident response plan.
Key Components of an Incident Response Plan
Your incident response plan should include:
- Incident detection and reporting procedures
- Investigation and analysis processes
- Post-incident review and lessons learned
9. Monitor and Analyze Security Logs
Continuous monitoring of security logs is essential for identifying potential threats. Organizations should:
- Enable logging for all cloud resources and applications.
- Utilize SIEM solutions to aggregate and analyze log data.
- Set up alerts for unusual activity or policy violations.
Log Management Best Practices
Follow these best practices for effective log management:
- Implement a centralized logging solution.
- Regularly review logs for anomalies.
- Ensure compliance with data retention policies.
10. Stay Informed About Threat Landscape
Understanding the evolving threat landscape is critical for effective cloud security. Organizations should:
- Subscribe to threat intelligence feeds.
- Participate in security forums and communities.
- Regularly update security protocols to address new threats.
Key Resources for Threat Intelligence
Explore these resources for staying updated:
- National Cyber Awareness System
- US-CERT
- Cybersecurity and Infrastructure Security Agency (CISA)
In conclusion, the cloud offers numerous advantages for businesses, but it also presents unique security challenges. By implementing these ten strategies, organizations can strengthen their cloud security posture and protect their critical assets.
FAQ
What are the best cloud security strategies for businesses?
The best cloud security strategies for businesses include implementing strong identity and access management (IAM), ensuring data encryption both at rest and in transit, regularly conducting security assessments, utilizing multi-factor authentication (MFA), and adopting a zero-trust security model.
How can encryption enhance cloud security?
Encryption enhances cloud security by protecting sensitive data from unauthorized access, ensuring that even if data is intercepted, it remains unreadable without the correct decryption keys.
What role does multi-factor authentication play in cloud security?
Multi-factor authentication (MFA) plays a crucial role in cloud security by adding an extra layer of protection, requiring users to verify their identity through multiple means, thereby reducing the risk of unauthorized access.
Why is regular security assessment important for cloud security?
Regular security assessments are important for cloud security as they help identify vulnerabilities, ensure compliance with security policies, and adapt to new threats, thereby maintaining a robust security posture.
What is a zero-trust security model in cloud environments?
A zero-trust security model in cloud environments is a strategy that assumes that threats could be internal or external, hence it requires strict verification for every user and device attempting to access resources, regardless of their location.
How can businesses ensure compliance in cloud security?
Businesses can ensure compliance in cloud security by staying informed about relevant regulations, conducting regular audits and assessments, and leveraging compliance tools offered by cloud service providers to maintain adherence to standards.