As organizations embrace cloud-native architectures, integrating security practices becomes essential for agile teams. Just like a book mockup design helps in visualizing concepts, understanding cloud-native security requires a strategic approach from the initial design to deployment, ensuring robust protection against evolving threats.
In today’s fast-paced digital landscape, cloud-native applications have become the backbone of business innovation. Their rapid deployment and scalability are integral for agile teams seeking to deliver value to customers quickly. However, as organizations increasingly rely on cloud-native architectures, ensuring robust security measures becomes paramount. This article delves into the strategies, tools, and best practices for unlocking cloud-native security, enabling agile teams to operate confidently in a dynamic environment.
Understanding Cloud-Native Security
Cloud-native security refers to the approach of integrating security practices and tools at every stage of the cloud-native application lifecycle. This includes the initial design, development, and deployment phases, as well as ongoing monitoring and management. The goal is to create a security posture that is both proactive and responsive to the unique challenges posed by cloud environments.
Why Traditional Security Models Fall Short
Many organizations still rely on traditional security models that do not adequately address the complexities of cloud-native architectures. Here are some reasons why these models may be ineffective:
- Dynamic Environments: Cloud-native applications are built on microservices, which frequently change and scale in response to demand.
- Containerization: The use of containers introduces new security challenges, as traditional perimeter-based security does not apply.
- Shared Responsibility Model: In the cloud, security is a shared responsibility between the provider and the customer, often leading to confusion.
Key Components of Cloud-Native Security
To effectively secure cloud-native applications, organizations must consider several key components:
1. Secure Development Practices
Security should be integrated into the development process. This includes:
- Conducting threat modeling sessions to identify potential vulnerabilities in the design phase.
- Implementing code reviews and static application security testing (SAST) to catch security issues early.
- Utilizing dependency management tools to ensure third-party libraries are up to date and vulnerabilities are patched.
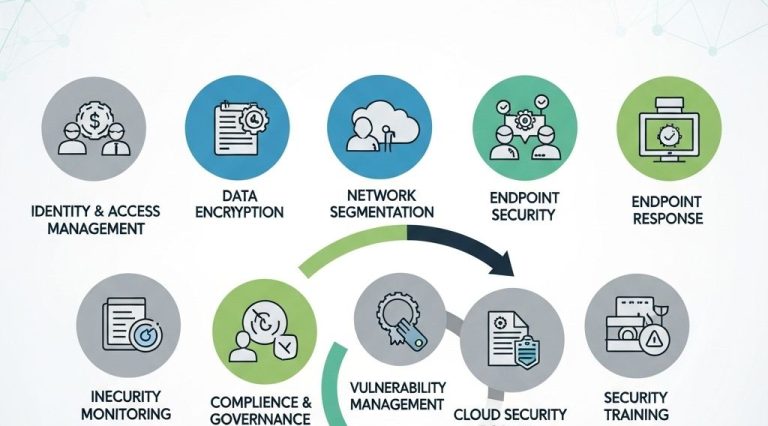
2. Identity and Access Management (IAM)
Managing user identities and controlling access to resources is crucial. Effective IAM practices include:
- Implementing role-based access control (RBAC) to restrict access based on user roles.
- Using multi-factor authentication (MFA) to add an extra layer of security.
- Regularly auditing access logs to identify and remediate unauthorized access attempts.
3. Container Security
Containers are a fundamental aspect of cloud-native applications. To secure them, organizations should:
- Use trusted images and maintain a secure image registry.
- Scan containers for vulnerabilities before deployment.
- Implement runtime security tools to monitor container behavior and detect anomalies.
Automation in Cloud-Native Security
Automation plays a pivotal role in enhancing cloud-native security. By leveraging automation tools, organizations can:
1. Continuous Security Monitoring
Automated security monitoring tools can continuously assess the security posture of cloud-native applications. Features to consider include:
- Real-time threat detection and alerting.
- Automated compliance checks against industry standards.
- Integration with CI/CD pipelines for security testing.
2. Incident Response Automation
In the event of a security incident, automation can expedite the response process. Strategies include:
- Deploying playbooks that automate the incident response workflow.
- Utilizing security orchestration tools to gather and analyze data from multiple sources.
- Implementing automated remediation processes to quickly mitigate threats.
Building a Culture of Security
Beyond tools and practices, fostering a culture of security within agile teams is essential for long-term success. Steps to consider include:
1. Regular Training and Awareness
Provide ongoing training to ensure that team members are aware of the latest security threats and best practices. This can involve:
- Hosting workshops and seminars on secure coding practices.
- Encouraging participation in security conferences and online courses.
- Sharing security news and updates in team meetings.
2. Collaborative Security Practices
Encourage collaboration between development, operations, and security teams (DevSecOps) to ensure that security is a shared responsibility. Methods include:
- Regular cross-team meetings to discuss security challenges and solutions.
- Integrating security metrics into team performance dashboards.
- Creating a feedback loop where security incidents are analyzed, and lessons learned are documented.
Leveraging Security Tools and Technologies
A robust security framework requires the right tools and technologies. Here’s a table of essential security tools for cloud-native environments:
| Tool Category | Example Tools | Purpose |
|---|---|---|
| Container Security | Twistlock, Aqua Security | Scan and secure container images |
| Identity and Access Management | Okta, AWS IAM | Manage user identities and access |
| Monitoring | Splunk, Datadog | Real-time threat detection and logging |
| Compliance | Qualys, Prisma Cloud | Automate compliance checks |
Conclusion
As cloud-native technologies continue to dominate the landscape, agile teams must prioritize security to protect their applications and data. By adopting a proactive security posture, leveraging automation, fostering a culture of security, and utilizing the right tools, organizations can unlock the full potential of cloud-native security. Embracing these practices not only enhances security but also builds customer trust and fosters innovation in a competitive market.
FAQ
What is cloud-native security?
Cloud-native security refers to a set of practices and tools designed to protect applications and data within cloud environments, enabling organizations to leverage cloud technologies securely.
How can agile teams implement cloud-native security?
Agile teams can implement cloud-native security by integrating security practices into their DevOps workflows, utilizing automated security tools, and fostering a culture of shared responsibility for security.
What are the benefits of cloud-native security for agile teams?
The benefits include faster deployment times, improved compliance, reduced risk of breaches, and enhanced collaboration among team members due to streamlined security processes.
What are common challenges in cloud-native security for agile teams?
Common challenges include managing dynamic cloud environments, ensuring consistent security policies, and addressing vulnerabilities in rapidly evolving applications.
How can organizations ensure compliance while adopting cloud-native security?
Organizations can ensure compliance by implementing automated compliance checks, maintaining thorough documentation, and continuously monitoring cloud environments for adherence to regulatory standards.
What tools are recommended for cloud-native security?
Recommended tools include container security solutions, cloud security posture management (CSPM) tools, and security information and event management (SIEM) platforms specifically designed for cloud environments.